Summary
Zoom supports Proof of Key Code Exchange (PKCE), pronounced “Pixy”, industry - standard protocol for authorization when requesting user tokens. This offers better security by enabling clients to use a code challenge and code exchange as part of the initial user authorization request. See rfc7636 for details.
What is PKCE?
PKCE is an extension to the OAuth 2 spec. Its design aims to add an additional layer of security that verifies that the authentication and token exchange requests come from the same client. This is achieved through the use of the code_challenge and code_verifier parameters, sent by the third-party application during the OAuth process.
![]() The
The code_verifier parameter’s value uses the SHA 256 Cryptographic Hash Algorithm. SHA 256 creates a unique “signature” for a text or file of any size,
![]() The
The code_challenge Base64-encodes the value generated from the code_verifer step.
 Note:
Note:
-
Regardless of the input file or text, the generated value is always the same length
-
Guaranteed to be always produce the same result for the same input
-
One way (that is, you can’t reverse engineer it to reveal the original input)
-
Code_challenge value should be equivalent to the
code_verifierparameter’s value when using the “plain” code challenge mode, or a cryptographic hash of thecode_verifierparameters’ value, though the use of the “plain” code challenge method is largely discouraged.
Generate the Code_verifier and Code_challenge:
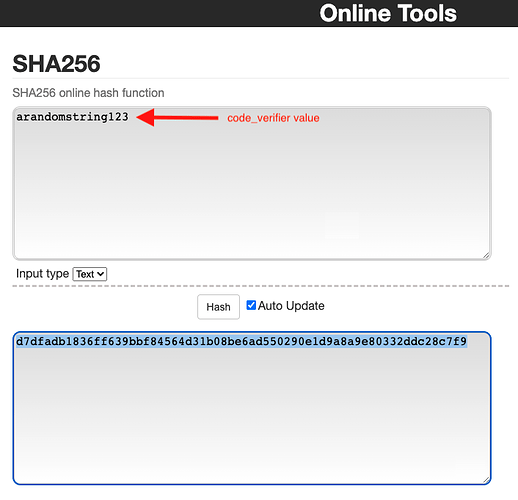
![]() You can manually generate the code_verifier by entering a random string into the SHA256 online tool on Github:
You can manually generate the code_verifier by entering a random string into the SHA256 online tool on Github:
SHA256 Tool Screenshot:
![]() Then, manually encode the encrypted value with the Base64 online tool:
Then, manually encode the encrypted value with the Base64 online tool:
Base64encode Tool Screenshot:
Programmatically generate the Code_verifier and Code_challenge
Alternatively, you can programmatically generate the Code_verifier and Code_challenge with the following script:
mkdir crypto-gen
cd crypto-gen
npm init -y
const crypto = require("crypto");
const btoa = require('btoa');
function base64URLEncode(str) {
return str.toString('base64').replace(/\+/g, '-').replace(/\//g, '_').replace(/=/g, '');
}
function sha256_ASCII(buffer) {
return crypto.createHash('sha256').update(buffer).digest('base64').toString("ascii");
}
const code_Verifier = base64URLEncode(crypto.randomBytes(32));
const code_ChallengeUrlSafeEncode = base64URLEncode(sha256_ASCII(code_Verifier));
console.log("code_verifier: " + code_Verifier);
# Append trailing "=" to the end code_challenge_url_safe_encode
console.log("URL safe encode code_challenge : " + code_ChallengeUrlSafeEncode + "=");
PKCE Flow Overview
![]() During the initial step (
During the initial step ( https://zoom.us/oauth/authorize ) of the OAuth procedure, the code_challenge parameter is provided by the third-party client to the OAuth provider.
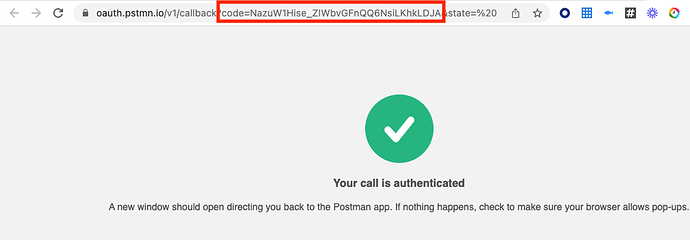
![]() After the user has manually authorized the application, the OAuth provider should then respond with an authorization code, which must be returned to the OAuth provider along with the
After the user has manually authorized the application, the OAuth provider should then respond with an authorization code, which must be returned to the OAuth provider along with the code_verifier parameter, by the third-party client, in exchange for an access token.
![]() If the
If the code_verifier parameter does not match the code_challenge provided by the client in the initial authorization request, this may indicate an attempted code injection attack, and so the OAuth process should be abandoned by the provider and an error returned to the third-party client.
![]() If Zoom verifies that the
If Zoom verifies that the code_challenge and the code_verifier match, the token endpoint (https://zoom.us/oauth/token) continues processing.