We are in the process of updating our Meeting SDK on the Zoom Marketplace. This app is not intended to be published. There is no plan to use the Zoom Api’s. The sdk’s used for native ios and android in a healthcare app.
We have a Test and Production app.
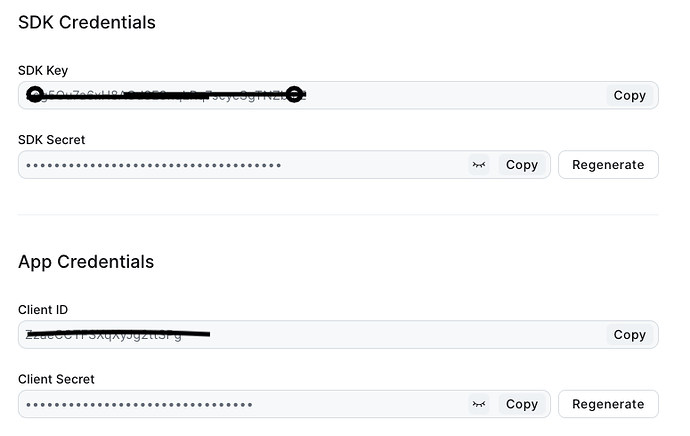
We noticed the Sdk Credentials or App credentials work the same from a sdk functionality. Is this by design?
authService = MobileRTC.shared().getAuthService()
authService.clientKey = SDK Key or Client ID
authService.clientSecret = SDK Secret or Client Secret
For the “Redirect URL for Oauth” or add Allow list . We don’t have a end point at the moment. We just put a valid urls to our company. Since the Oauth is for Zoom API’s this should be ok?
For the last part when we hit “Add” the page redirects to our valid url.
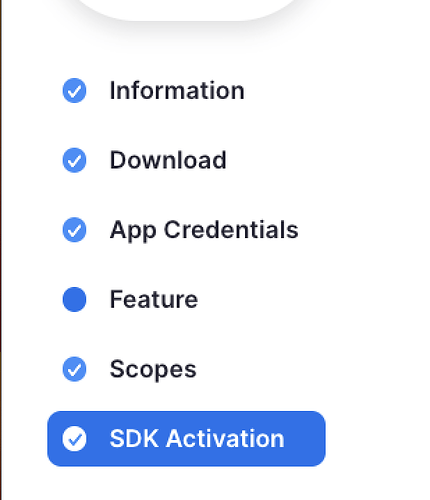
We noticed in our production non updated meeting sdk app. There is a green “Your app is activated”.
Our updated one just has all the checkmarks, but not the green “Your app is activated” Our testing shows our app works without being activated. Is there any thing to be concerned with not being activated?